Zero In on Evidence Faster — recognized around the world as the standard in computer forensics software
With the growth of big data from the wide variety of devices and systems, it can be challenging to find and collect relevant evidence in a timely and efficient manner. Whether you are law enforcement dealing with the growing backlog of devices waiting to be processed or a company searching through massive amounts of data from multiple sources, FTK® cuts down on investigation time and resources needed by providing you with an integrated forensics solution preferred by expert digital investigators.
Features
FTK allows users to create images, process a wide range of data types from forensic images to email archives and mobile devices, analyze the registry, crack passwords, and build reports—all within a single solution.
- Remote Machine Analysis: With the single-node enterprise, users can preview, acquire and analyze evidence remotely from computers on your network.
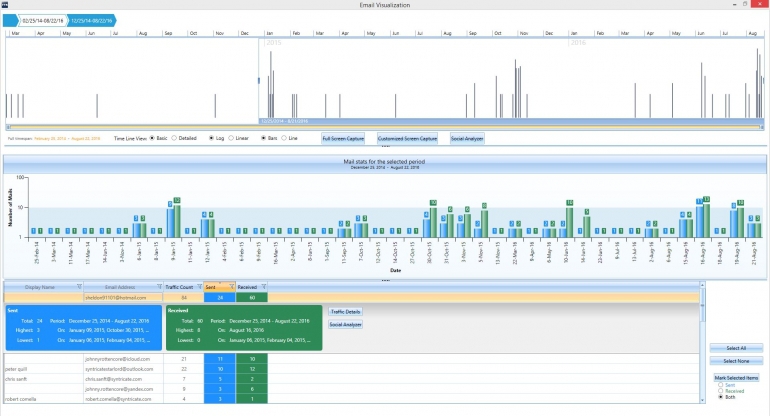
- Visualization: Automatically construct timelines and graphically illustrate relationships among parties of interest in a case. With Email, Social and File Visualization you can view data in multiple display formats, including timelines, cluster graphs, pie charts, geolocations and more, to help you determine relationships and find key pieces of information. Then generate reports that are easily consumed by attorneys, CIOs or other investigators.
- Internet Browser and Web-Based Email Evidence: Almost every investigation involves the analysis of Internet artifacts. Web browsing caches store records of sites a suspect has visited, web-based emails may help to prove intent or correlate other events and instant message conversations or social media sites can contain evidence. When evidence is processed, artifact files are categorized and organized so that you can easily see them.
- Password Cracking and Recovery: Unlock files when you don’t know the password with market-leading decryption password cracking and recovery.
- Explicit Image Detection (EID): Image detection technology recognizes flesh tones and auto-identifies more than 30,000 potentially pornographic images.
- Malware Triage & Analysis: Available as an option to FTK, Cerberus is an automated malware triage platform solution designed to integrate with FTK. It’s a first layer of defense against the risk of imaging unknown devices and allows you to identify risky files after processing your data in FTK. Then you can see which files are potentially infected and can avoid exporting them. Cerberus is one tool in your malware arsenal and helps you identify potentially malicious files.